Avert Data Breaches with Document Encryption
Benefit from the value of commodity storage, while continuing to use your own third-party encryption technology. Secure your valuable digital assets with the highest level of encryption available in today’s market. With our unique hybrid approach to encryption, you can entrust your data is stored within a secure environment.
ENCRYPTION BENEFITS
Encryption has to be highly secure, easy to use and quick to deploy. The combination of perpetually-on encryption that is simple to use for business, and also efficient for administrators to manage, provides organizations of all sizes for the benefits of encryption without compromise.
Security
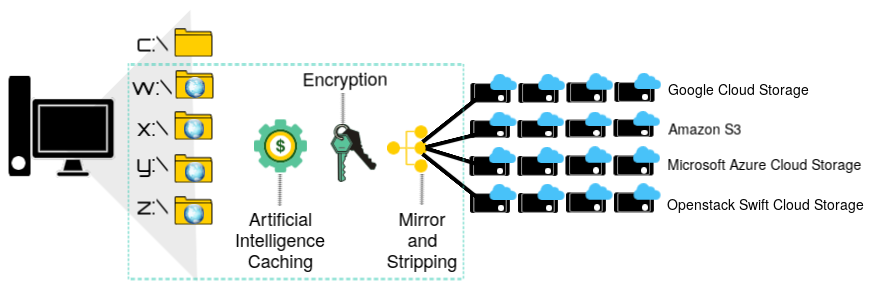
Data is encrypted in real time, on the fly during transmission to the cloud storage provider, and at rest, both at the provider and locally, ensuring that third parties cannot make sense of data.
AI Availability
Incorporates an artificial intelligence engine to optimize local caching of data from virtual drives. The AI engine learns how each user works with files, profiling each user’s individual activity. The system can predict which files each user will need, and cache those files on local storage.
Hybrid Flexibility
Cloud-provider-agnostic, and support for on-premise as well, enables a single virtual drive to use storage from different clouds. Access is unrestricted from any location, eliminating the need for additional hardware VPNs or tokens.
Compliance Standards
Strong encryption and obfuscation scheme is compliant with all current security mandates for PCI DSS, HIPAA, CASB1386, GLBA, DoD 5015.2, and other data protection regulations.
AGGREGATION & MIGRATION
Enables administrators to aggregate unlimited cloud storage from multiple providers to create virtual drives that scale to fit the needs of any organization. Administrators can build a storage pool by spanning data across multiple storage containers for performance and bandwidth aggregation.
Effective & Easy Encryption
Deploy encryption requiring no change in user behavior by utilizing the native OS file structure. Encrypted virtual drives appear to your users just as a standard network drive. Use web services APIs, to provide tight integrations with current storage systems, providing a higher level of data security.
HOW ENCRYPTION WORKS
Our strong encryption and obfuscation scheme is compliant with all current security mandates; PCI DSS, HIPAA, CASB1386, GLBA, DoD 5015.2, and other data protection regulations. If a cloud storage admin account is compromised, malicious actors virtually cannot re-assemble and decrypt the data.
Step 1
Data is encrypted locally, then stripped of its digital identity.
Step 2
Using a patent-pending algorithm, data is sliced into indiscriminate fragments.
Step 3
Each fragment is arbitrarily named then issued a unique security key.
Step 4
Fragments are scattered across randomly generated directories.
Step 5
Data transmitted to cloud storage is again encrypted over the wire using secure Internet data transmission protocols.
Step 6
Data is encrypted at rest in the cloud using the cloud storage providers’ native encryption schemes.
Data Security Breaches In The News
FedEx
“FedEx says cyber attack to hurt its 2018 results. Package delivery company FedEx said its 2018 results would be hurt in part due to disruption of operations at its TNT Express unit as a result of a cyber attack in June. ” – CNBC
Equifax
“We’ve seen a $6 billion loss in market cap, estimated losses from these breaches in excess of $20 billion,“ – Mark Grossman, Security Expert
Uber
“Five state attorneys general are investigating Uber breach. Uber is also now under investigation by at least five state Attorney General offices and has been named in multiple lawsuits.” –
The Risk Of Data Breaches
Massive data breaches are in the news almost daily. It’s alarming to realize those are just the publicly disclosed cases. Imagine for a moment, how much data has truly been compromised. Often, the true gravity of a breach is not discovered for days, weeks or months. And in certain instances, even years. Don’t become another data breach statistic. Strong hybrid data encryption technology is here, and when it’s so easy and affordable to use, why wouldn’t you?
Risks
Risks Associated With Data Breaches
Security breaches have become a common occurrence. Smartphones, tablets, Windows desktops, application servers, and infrastructure-as-a-service providers are all susceptible. Attacks affect both small and large organizations indiscriminately. The consequences can be devastating to operations, company reputations, and financial accounts. The cost of a data breach may include resuming operations and addressing the security gaps that caused the breach. However, legal liability and regulatory fines can be a tremendous burden as well.

DATA RECORDS LOST OR STOLEN SINCE 2013
DATA BREACH STATISTICS
ONLY 4% of breaches were “Secure Breaches” where encryption was used and the stolen data was rendered useless.
For more in-depth breach statistics, see the frequency rates of lost or stolen records, below and join our newsletter on how Avert Data Breaches with Document Encryption.
